Protect Data in Mobile & Web Apps Using Encryption
Mobile devices capture 55% of the website traffic. This enhancement in mobile website traffic as well as mobile web applications over the coming years is due to two main factors. Firstly, the transformation of the physical market to a digital platform (for better customer reachability and for gaining better revenues), and secondly, due to the Covid-19 pandemic.
Both these factors have enhanced mobile and web applications and have compelled IT specialists and cyber security personnel to ensure their data security through Web Application Testing. Hackers are too smart and tech-savvy to penetrate these devices and misuse their data and hence it's essential to secure this mobile app and site data against these cyber-thieves by implementing stringent data web app security measures.
Web Application Testing, including comprehensive mobile app testing, plays a crucial role in identifying vulnerabilities and ensuring the security of mobile and web applications. By conducting comprehensive testing, including penetration testing, vulnerability scanning, and security audits, organizations can proactively detect and fix security loopholes before they can be exploited by malicious actors. Regular Web Application Testing helps maintain the integrity and confidentiality of user data, preventing unauthorized access and data breaches.
About Mobile & Web App Data Security:
Mobile and custom web app data security is all about securing each endpoint to prevent phishing attacks, malware, data breaches, and other malicious intrusions. In short, the main motto of mobile web security is to ensure data integrity and data confidentiality of user data. If you suspect that your device is compromised, it is crucial to take steps to remove phone virus to protect your data.
This motto can be achieved by encrypting data.
What is Data Encryption?

Data encryption is a process wherein the data is encoded during the communication process. Encryption security uses cryptographic algorithms to transform plain data into a cipher form that looks like a code. This cipher code can be decrypted with a special key which is possessed by the intended recipient only.
Encryption may at times fail to prevent unwanted access but is effective in ensuring data privacy, especially when paired with user awareness of phishing attempts that aim to bypass encryption altogether.
In addition to encryption, integrating a password manager can further safeguard sensitive information by creating and managing complex passwords that are difficult to breach.
In the current scenario, data encryption is the most effective and popular digital security solution used by organizations, especially for any mobile app development company like Halo Digital building secure digital products.
Methods:
There are two methods of encrypting data.
· Symmetric Encryption – wherein a single key is used for the encryption/decryption process.
· Asymmetric Encryption – wherein two different keys are used in the encryption/decryption process. A public key is for encryption while a private key is for the decryption process.
As far as the encryption algorithms are concerned, the most common one is the AES (Advanced Encryption Standard) encryption algorithm which uses 128-bit, 192-bit, and 256-bit keys to encrypt and secure data.
Now that we have a clear idea of encryption and its importance, let’s check out where this robust security solution can be implemented.
The Three States of Mobile and Web App Data:
To secure your digital empire it's essential to know when and where can this digital security solution be applied. Varied clients have varied security needs to protect their confidential data. In this stage, using reliable Smartsheet alternatives can optimize collaboration but also ensure data security.
Some need mobile data security, whereas others need server data/file security, to prevent intruders from accessing their data. Some clients need cloud security for stored data, whereas some need security during data transfers. To fulfill all these security requirements of varied customers, it’s essential to focus on the states of data.
Three states of data can cover all the client requirements. The pivotal motto of all these states is to ensure data integrity and data privacy. Let’s check them out.
1. Data at Rest:
![]()
Data at rest as the name specifies refers to the inactive data. The examples include the data which is stored in databases, servers, flash drives, hard disks, cloud, etc. Many companies now a days switch to SQL Server to Snowflake for better storage performance.
The data which is stored on a physical or external device is termed data at rest.
2. Data in Transit:
![]()
When the data is moved from one location to another it is termed as data in transit.
When the data is moved from one location to another, it is termed as data in transit. This includes the data exchanged between the server and the browser, as well as data shifted from one location to another. In such scenarios, considering the use of a VPN service can add an additional layer of security. A VPN encrypts data as it travels, making it less vulnerable to interception or hacking during transit.
3. Data in Use:
![]()
All the active data which is regularly accessed, processed, modified, or deleted by the concerned is termed as the data in use.
With hackers on the prowl everywhere, it’s essential to secure all these three states of data and ensure that they are not vulnerable to cyber-attacks, such as spear phishing.
Why Security is Essential for Mobile and Web App Data?
Strong security is extremely vital for app data (and any web app development company), and hence it should be placed on the topmost priority list. Any security lapse in such cases may not only lead to the organization facing costly lawsuits, and paying heavy penalties, but can also lead to damaging of brand reputation and breaking of user trust. To enhance data security and manageability, consider migrating data from SQL Server to Snowflake. This transition leverages Snowflake's advanced security features and scalable architecture, providing a secure and efficient environment for handling sensitive data and maintaining compliance.
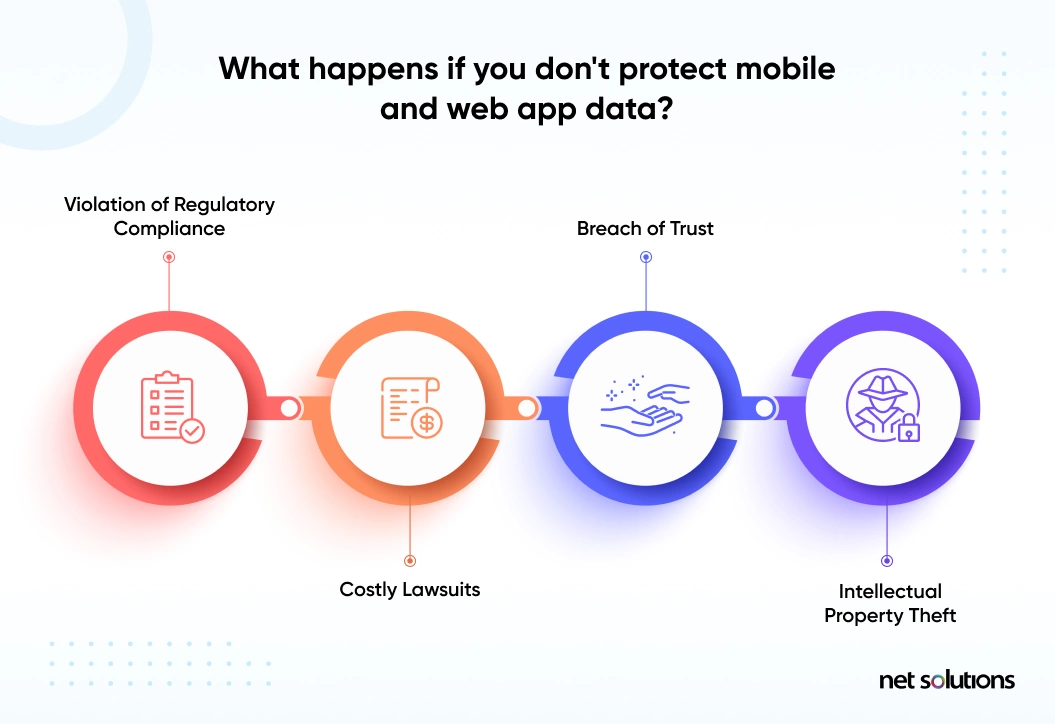
This loss is irreversible and hence it's vital to ensure end-point security of all data states.
Apart from these damages, securing mobile and web app data is essential as per Compliance Standards.
About Mobile Data & Web App Compliance:
There are varied compliance regulations which are set by the government and as per law which the companies need to adhere to. As stated above, failure to comply with the standard regulations may lead to heavy penalties, audits, and lawsuits.
Data compliances influence data integrity, data storage, data usage, and data collection—which should be protected in a sustainable data center that ensures server uptime. This data includes all the sensitive stuff, secured health care data, financial details, and PII (personally identifiable information).
The same stands true for web and mobile apps. Irrespective of where the mobile application is created, it must follow all the defined regulatory requirements relating to data security and end-user privacy. Ensuring a seamless mobile app experience requires careful consideration of these regulatory aspects.
The entities which enforce these data compliances are the GDPR (General Data Protection Regulation), CPRA (California Privacy Rights Act), CCPA (California Consumer Privacy Act), and PIPEDA (Personal Information Protection Electronic Documents Act).
Difference between Mobile App Security & Web App Security:
Both mobile apps and web apps can be accessed from smartphones, but there is a difference between these two terminologies.
According to a web app developer at Simpalm, "In web apps (at the front end), only a tiny portion is accessible to the user as the application runs on the server, whereas a mobile app development company (at the back end) is downloaded and installed on the device.
· The app store approves mobile apps, whereas web apps can be easily browsed via browsers and don’t require any special approval.
· Mobile apps are better secured as compared to web apps.
About Web App Security:
Web apps can be secured with traditional security tools like web application firewalls (WAFs), dynamic application security testing (DAST) tools, and static application security testing (SAST) tools. By working with a nearshore development team, businesses can access specialized security expertise at a lower cost, ensuring comprehensive protection for their web applications.
Web apps also use SSL/TLS (Secure Socket Layers / Transport Layer Security) certificates for creating encrypted tunnels between two networks. This digital certificate is issued by a Certificate Authority (CA) and ensures the site's authenticity and the owner’s identity before its issuance. Once it’s installed on the website, it establishes an encrypted tunnel for all browser-server communications.
Example:
Wildcard SSL certificate or SAN or Multi-domain SSL certificate helps in securing multiple subdomains and domains of the web app with encryption security. An app developer can go with the lowest or cheap SAN SSL or wildcard cert for app security. When considering the security measures for your app, it's essential to remember that hiring an experienced app developer is crucial.
About Mobile App Security:
In contrast to these security tools, mobile apps are installed on mobile devices after being downloaded from the app store. These apps are bound to be more vulnerable as they face external threats like malware and other digital frauds. These apps are loaded with sensitive data and any data breach or unauthorized access should be prevented. This could include providing access to health resources such as weight loss medication like semaglutide tablets or other ailments that not only have a mental but physical effect.
Research indicates that 85% of these apps have security and privacy lapses.
Mobile app security can be strengthened by securing all the data states, endpoints, and other open gateways with strong encryption security. Additionally, when building robust and secure mobile applications, it's often beneficial to hire an AI mobile development company or hire flutter app developers who are well-versed in implementing advanced security measures. Flutter example apps can also provide valuable insights and best practices for enhancing the security of your mobile application.
How to Secure the Data in Mobile & Web Apps Using the Encryption Technology?
Encryption is the sole solution that not only meets all the compliances but guarantees a secured app for customer data privacy. A custom web application development company can implement these encryption practices effectively, ensuring robust security tailored to specific business needs. Hence, to address shopper security concerns, mobile app developers have resorted to encryption security to prevent unwanted digital dangers.
Incorporating Sitecore development services into your digital strategy can enhance both security and user experience. A Sitecore development agency ensures your web and mobile apps maintain robust data protection while delivering personalized content. To fully leverage these benefits, it's crucial to hire mobile app developers with the right expertise.
Best Encryption Practices:
1. Source Code Encryption:
Smart hackers directly attack the source code to gain control over the application. There are two types of source code attacks carried out by these cyber-criminals.
· The attacker uses malware or bugs to penetrate the code and destroy it.
· The attacker breaks the code and infuses the app with malware for ignorant users.
In this way, the attacker can play with the code, modify it, and misuse it to gain unauthorized data access.
Source code encryption is the process of securing the source code by encrypting the strings and files of the web/mobile app against cyber theft and intruder access.
In short, securing the code as so to prevent the intruders from gaining control of the code, modifying them, misusing them, deleting them, or making it non-readable is termed source code encryption.
2. Manage Keys Securely:
Encryption is meaningless if you can’t keep your keys secure.
The next step is to ensure the best key management practices. These include securing the cryptographic keys (private key & public key) which are used in the encryption/decryption process at all stages. The stages include the generation of keys, exchanging of keys, storage of keys, usage of keys, and replacement of keys when expired. Ensure the key security at all these stages.
This is particularly crucial when performing sensitive transactions online, such as when you buy bitcoin with debit card or check the bitcoin price today, where robust key management practices help protect your financial data from unauthorized access.
Key Management Best Practices:
· Develop strong key management policies and systems.
· Select the appropriate encryption algorithm and the key size as per your business requirement.
· Authorize your keys to ensure restricted access. Also, ensure a fixed time for its use to prevent security lapses.
· Secure the dedicated servers and restrict their physical access.
· Destroy unused keys for preventing unauthorized entries.
· Utilize an external key management system like a hardware security module (HSM), etc., or other hardware devices to ensure that the location of the data and keys are different.
· Restrict the access of keys to a few legit and reliable users.
· Update/Rotate these keys regularly for better security.
3. File Level & Database Encryption:
Insecure data storage is a grave issue since it puts sensitive and confidential information (passwords, personal information, financial details, etc.) at risk of cyber breaches and such breaches can lead to lawsuit or even a class action Lawsuit against a company as personal data of a number of people get stolen. Such lawsuits leads to hefty settlement and reputation of company also gets harmed.
If your data was leaked in one of such cyber security breach but you did not had the right knowledge or means to get compensated then you can check with your lawyer to get assistance to claim unclaimed money class action settlements.
Research by Synopsis indicates that 76% of mobile apps are loaded with insecure data storage.
To address this critical issue and protect your company from such lawsuits, all this unstructured data must be removed from the mobile device and stored in local files and other internal/external databases. The rest of the data should be encrypted for preventing unwanted entries. Using insider threat software can also strengthen your security by detecting potential internal risks and safeguarding sensitive information.
4. Utilize the Latest Cryptographic Techniques:
Hackers keep on making advances to penetrate mobile and web apps by breaking existing securities. To ensure strong encryption security, web security designers should be consistent in their cryptographic patterns, and try to monitor and test them regularly.
Although AES (Advanced Standard Encryption) is the trusted security standard acknowledged by the US government, the new emerging standards like ECC (Elliptic Curve Cryptography) are already being accepted and acknowledged by NSA.
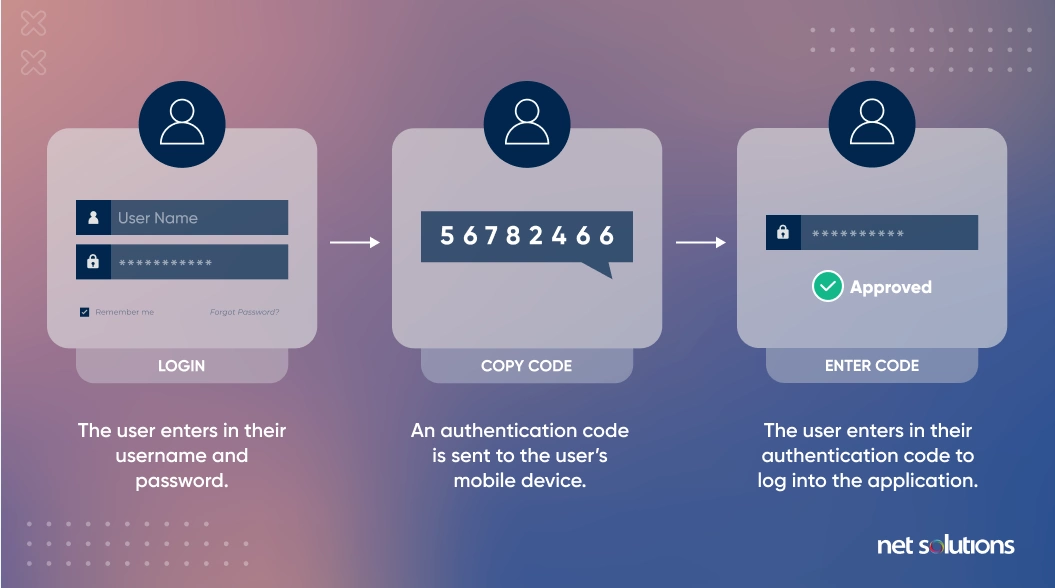
5. Multi-Factor Authentication (MFA):
Another security solution like MFA, parallel in line with encryption security will help in tightening the mobile app development company security. MFA is essential in all cases be it internal employees or external parties. This security solution helps in restricting user access by authenticating the users.
Example:
MFAs like the hardware token provide dual authentication and offers strong mobile and web app security is established.
Hardware Token
6. Use FIPS 140-2 for Government Apps:
Federal Information Processing Standard Publication (FIPS 140-2) is a security standard of the US government which is used for approval of cryptographic modules (both hardware and software components). FIPS 140-2 uses four levels of security to secure government applications and their sensitive data.
Wrapping Up:
For implementing the best encryption practices to ensure mobile and web app security it's vital to understand the database and the company’s technologies. Leverage them and identify the sensitive data for securing it.
Limit the data access rights to a minimum number of users for preventing security vulnerabilities. Use encryption technology to prevent code/data modification and misuse.
Encrypt the mobile and web app data at all states and secure the app with a PIN or password. Utilize encryption security at all data states and monitor it regularly.
Last, but not least, backup your entire data on an external hardware device, so that the data can be recovered in case of surprise data breaches.